It Is Time To Ditch SMS 2-Factor Verification
Table of Contents
It’s 2018, and it’s time we understand that SMS 2-factor authentication is not a good way to double-check the users’ credentials. It’s been shown many times that phone numbers can be compromised.

The problem #
Here are just some examples of how cellphone number and customer data can be at risk:
| Security Issue | Date |
|---|---|
| T-Mobile exposes endpoint with account details | October 2017 |
| Cellphone accounts hijacked to go after cryptocurrency owners | August 2017 |
| Hackers able to hijack cellphone accounts | July 2017 |
| Thieves able to port cellphone numbers | March 2016 |
I can go on. The problem is so bad that the US Federal Trade Commission issued its own blog post documenting how these schemes work, referencing the Red Flags Rule guidance. And yet, we are proven over and over again that social engineering works against the consumer interests.
Phone numbers are not reliable. Phone numbers can be hijacked. Phone numbers change. Phone numbers stop working when you are traveling and not roaming. Phone numbers don’t work when you are using in-flight Wi-Fi. Phone numbers can stop receiving text messages/calls for a million of other reasons, effectively either (1) locking users out of an account or (2) compromising the account altogether. And, as last week has shown, something that was registered as a 2FA number can potentially be used for completely non-security reasons.
And yet, there are are still services that offer 2FA only through SMS.
What are the alternatives? #
There are several, and depending on the service, some might be more convenient than others. Outlook uses Microsoft Authenticator:
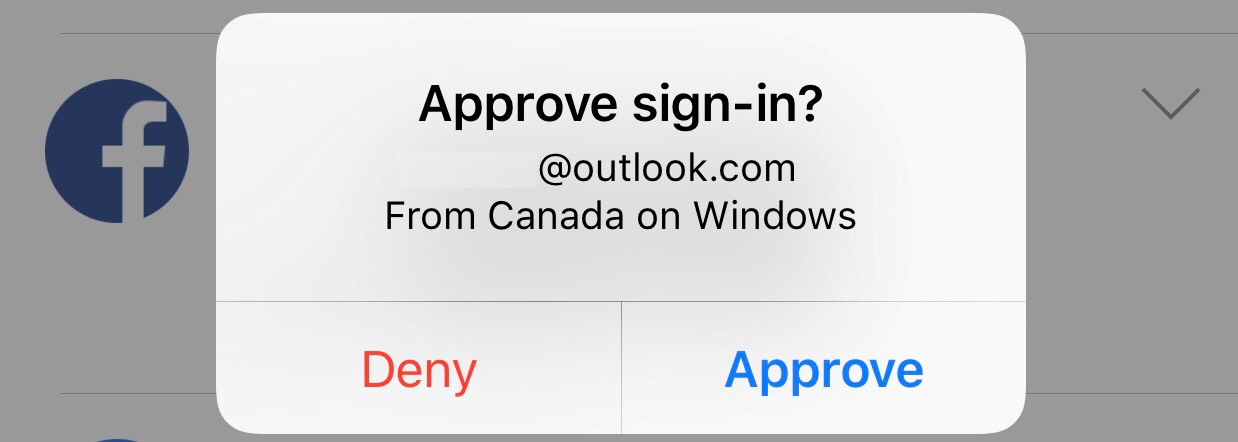
The way it works is it skips passwords altogether - once you connect the app to the account, you can remotely confirm the login by approving or denying the notification, and using TouchID (super-convenient, if you are on your iPhone) validating the request. This method stil assumes that your device has an active Internet connection
There are alternatives where you can confirm your identity even if the device where you are authenticating has an Internet connection, and the “second factor” does not - apps like Authy, Microsoft Authenticator (yes, it supports standard tokens that are refreshed every 30 seconds) or Google Authenticator solve the problem singlehandedly.
Or use U2F-compatible devices like the YubiKey which is probably the best way to go about secure authentication since it relies on a physical token be connected to the authenticating device.
These methods survive phone number changes, and the only way to compromise them is to be in physical posession of an unlocked device. Not to say that operational security is not important, because people will find a way to compromise even the token-based approach, but it still is magnitudes safer than relying on SMS messages or phone calls.
It’s by no means a trivial change on the provider side to properly implement token-based 2FA (either physical or numeric), but ultimately it will help users much more in the long run.
It’s time SMS 2FA goes the way of the floppy disk.