Reading Azure Active Directory Recommendations From PowerShell
Azure Active Directory (AAD) has a nifty feature that helps administrators (and those with the right privileges that are not administrators) to be able to keep tabs on the state of their tenant called Azure Active Directory Recommendations. Think of it this way - if there is something that requires the attention of an admin they would ordinarily need to write automation or custom rule sets to see whether there are items within that can potentially cause either risks or user inconvenience (such as way too many multi-factor authentication prompts).
Now, they can instead go directly to a tab from within the Azure Active Directory view in the Azure Portal and see the automatically-generated recommendations for their tenant.
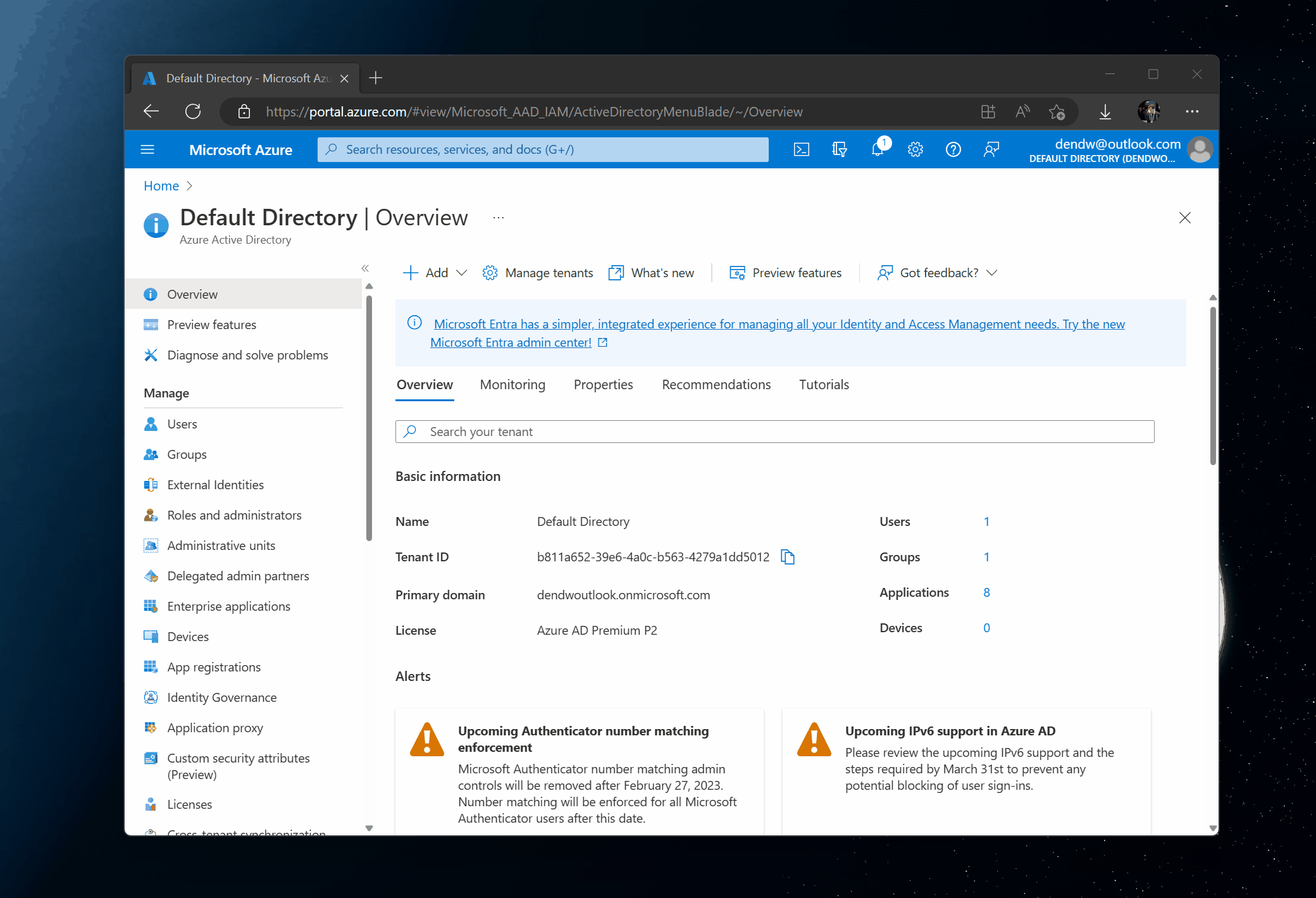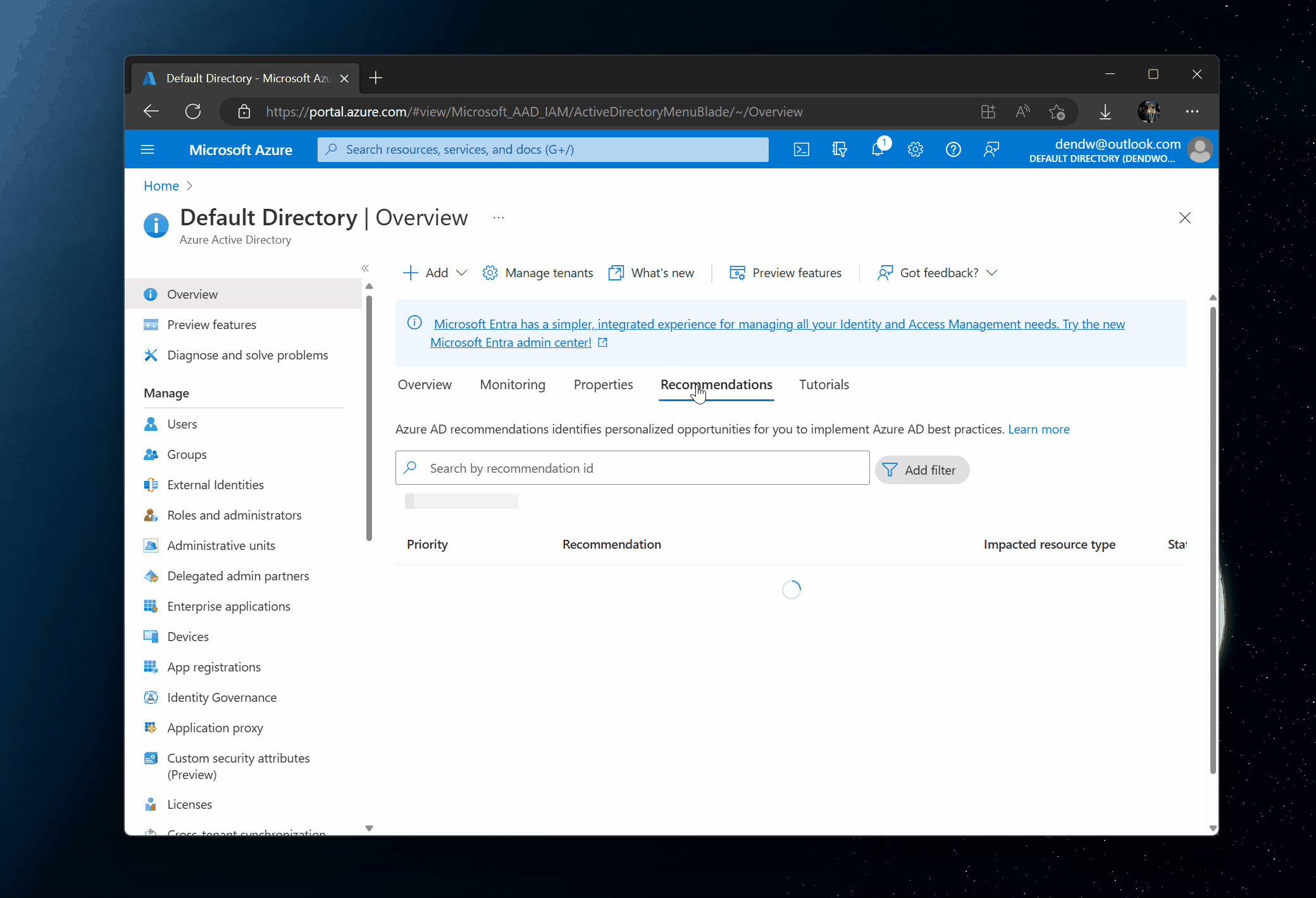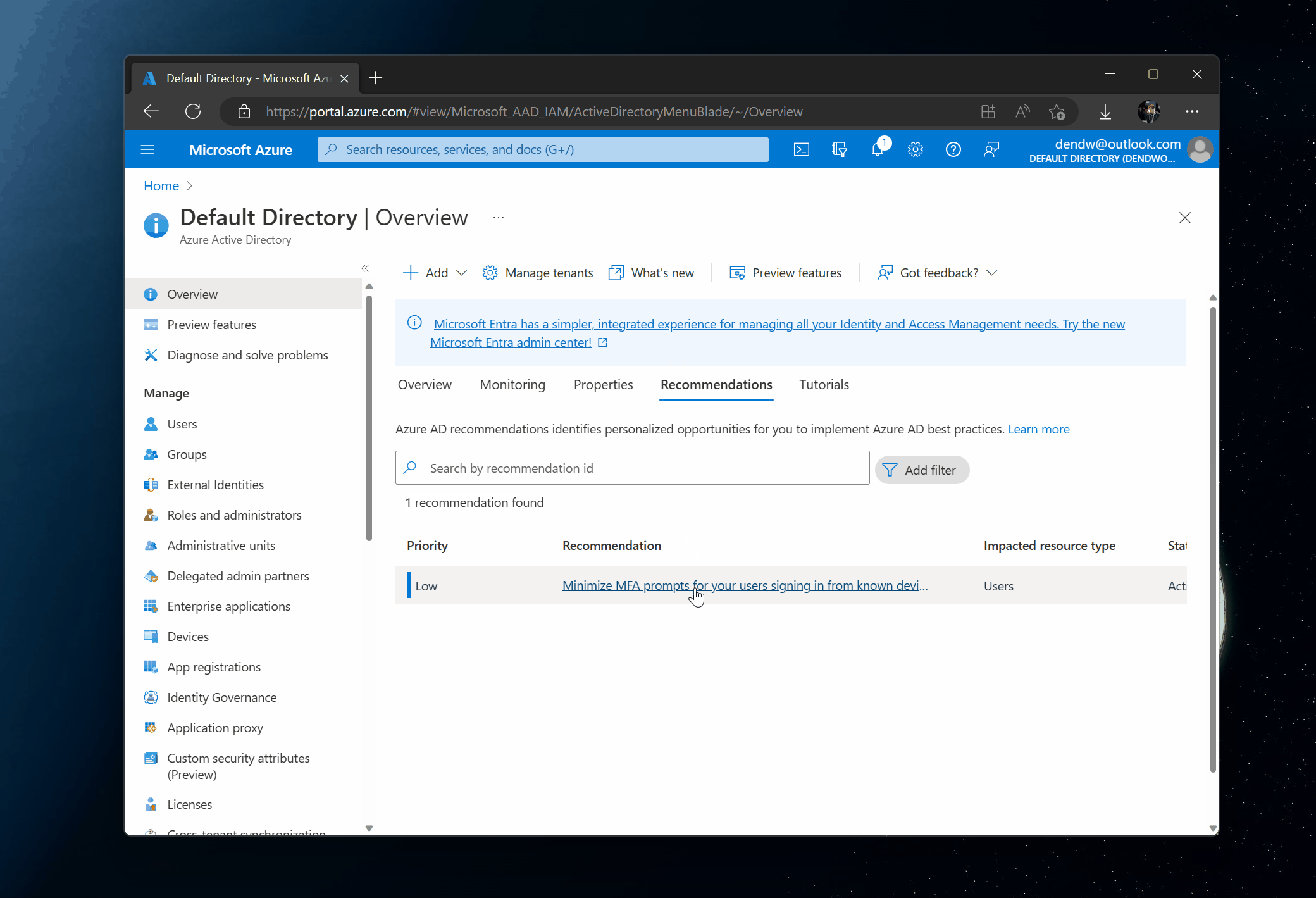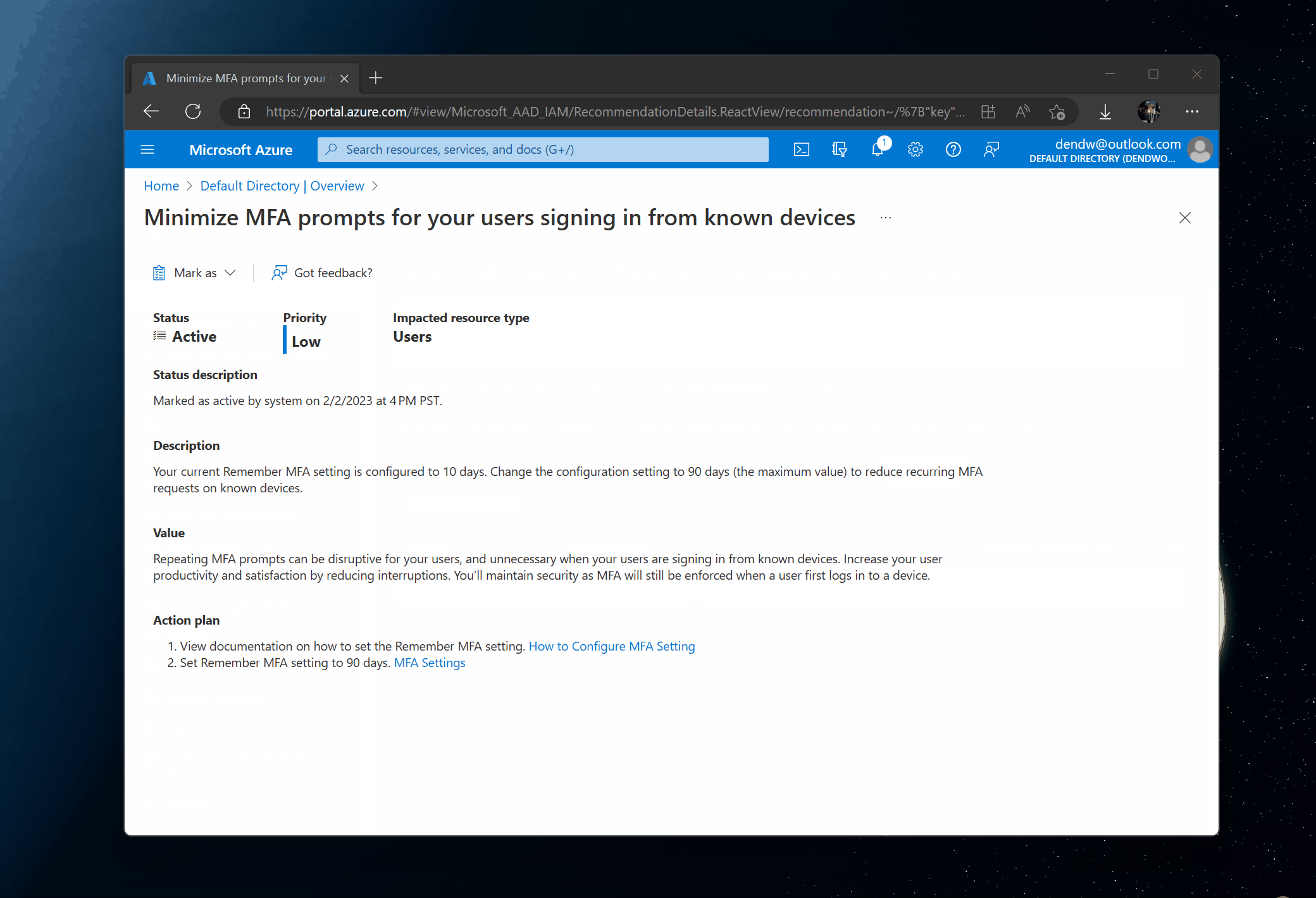
Seeing recommendations in the UI is great but I also tend to automate a lot of my workflows, so I naturally wanted to figure out how to access the data through something like PowerShell. The recommendations themselves are made available through the Microsoft Graph API, which can be seen if you open the Network tab in your browser when the recommendations are loading in the Azure Portal:
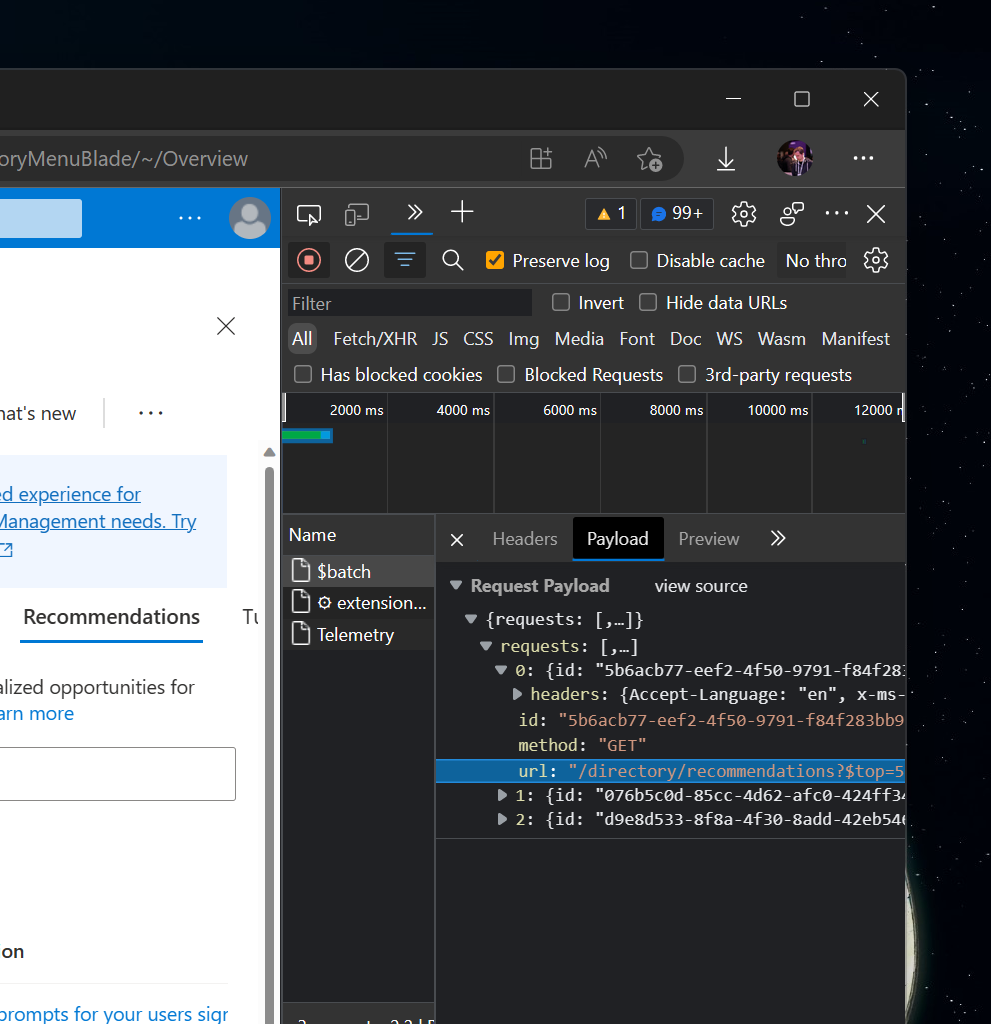
What this means is that I can replicate this experience myself if I can authenticate against the Microsoft Graph API (I’d need a bearer token). This is relatively straightforward if I use a something like Microsoft Authentication Library (MSAL) since it would handle most of the work for me. For now, though, I can extract the token from the Network tab and paste it into my Postman sandbox to be able to see what data the API returns.
I like Postman for this purpose because through it I can craft whatever REST request I want without fiddling with replays, editing the payload in the browser, and so on. If you’re working with REST APIs frequently, it’s an indispensable tool.
To get the recommendations, I would issue a request to:
https://graph.microsoft.com/beta/directory/recommendations
As I mentioned above, all I need for this request to succeed is a bearer token that is associated with my account that has access to directory recommendations.
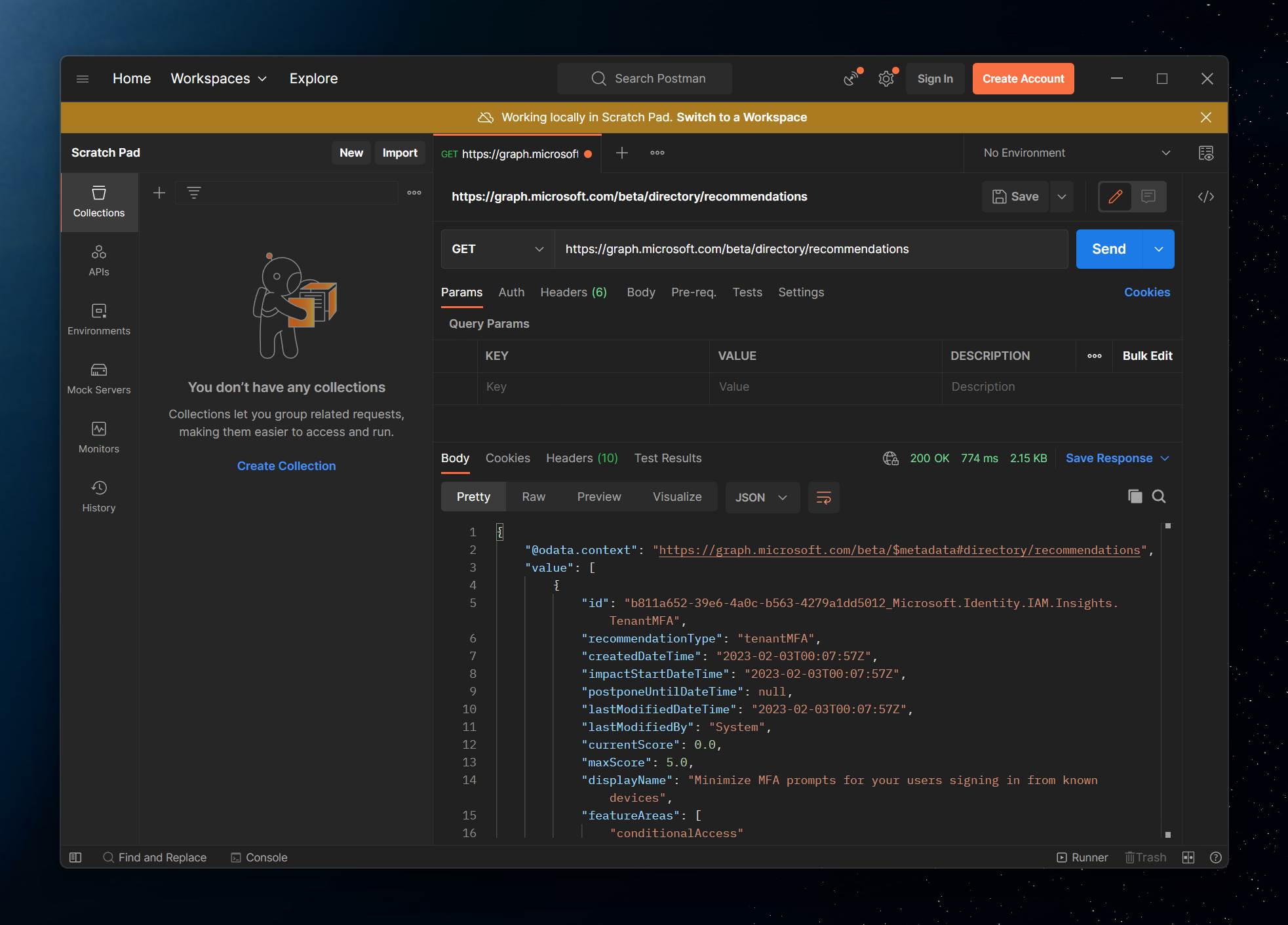
The request returns quite a bit of extra data about my recommendation that I can parse and make additional decisions on as a tenant admin. But what if there was a different way for me to do this even easier? Enter the Microsoft Graph PowerShell SDK. The SDK is effectively a reflection of the REST API with some nice additions that would enable me to handle certain things out-of-the-box, one of them being authentication.
The command I can run is:
Connect-MgGraph
-Scopes "DirectoryRecommendations.Read.All, DirectoryRecommendations.ReadWrite.All"
-Tenant MY_TENANT_ID
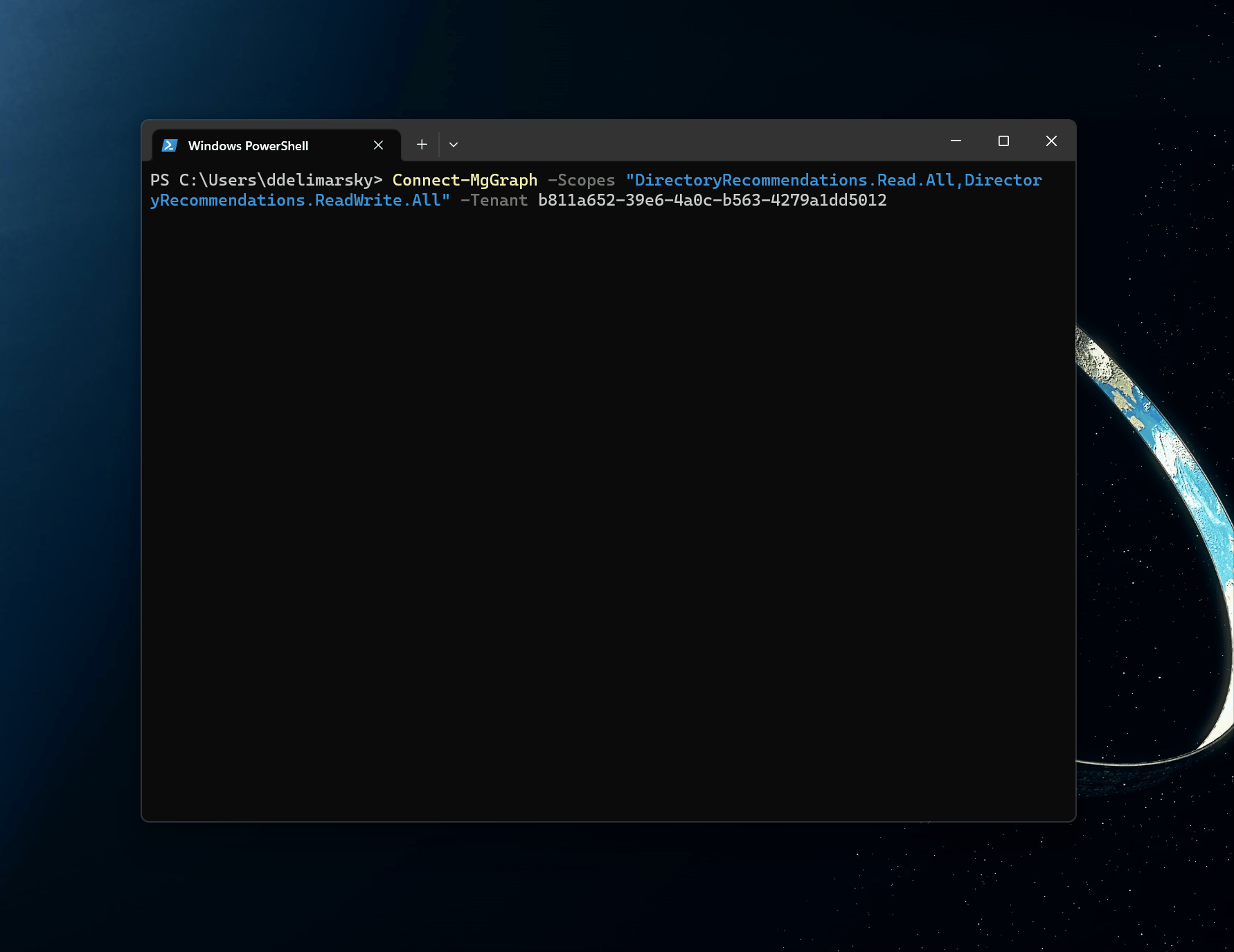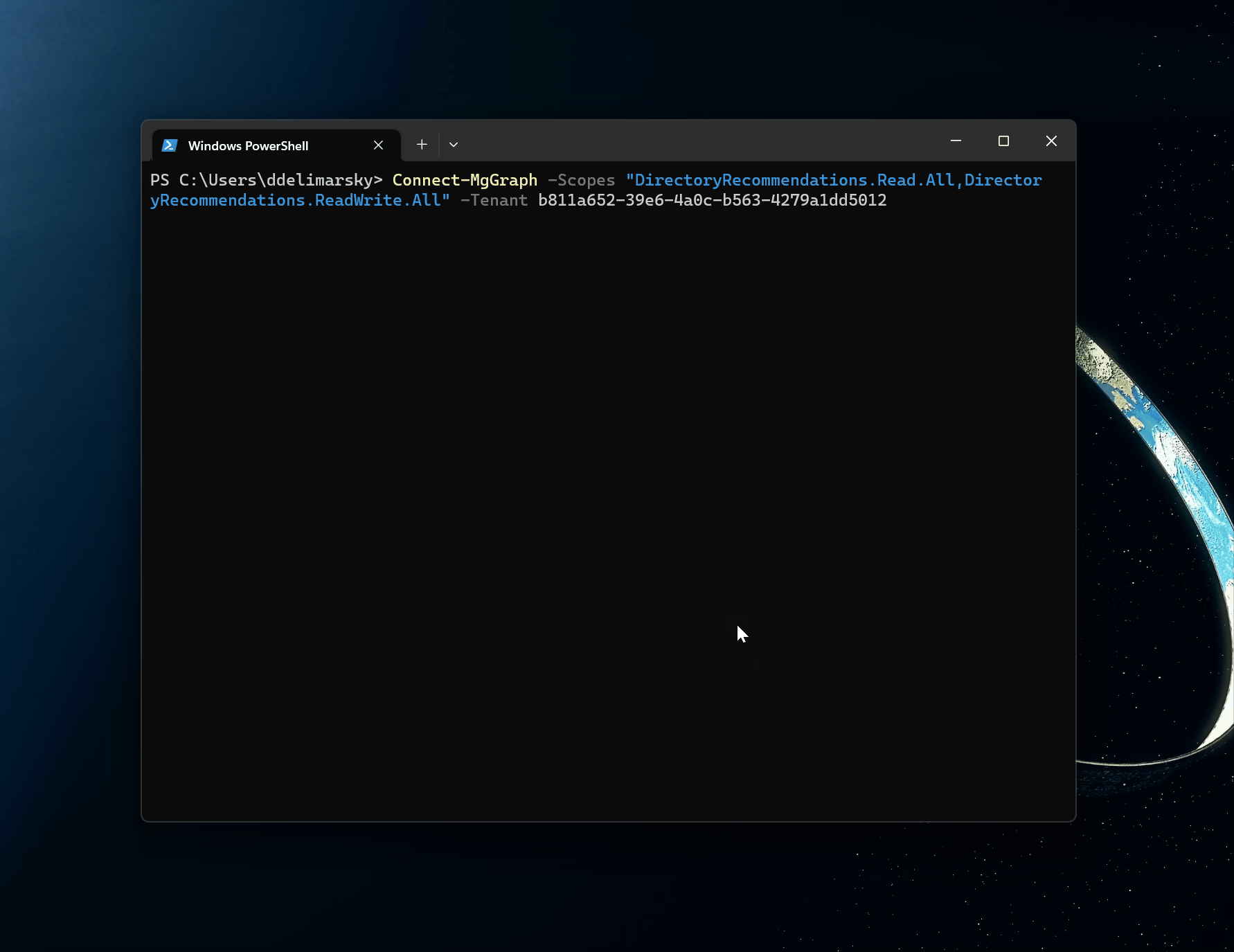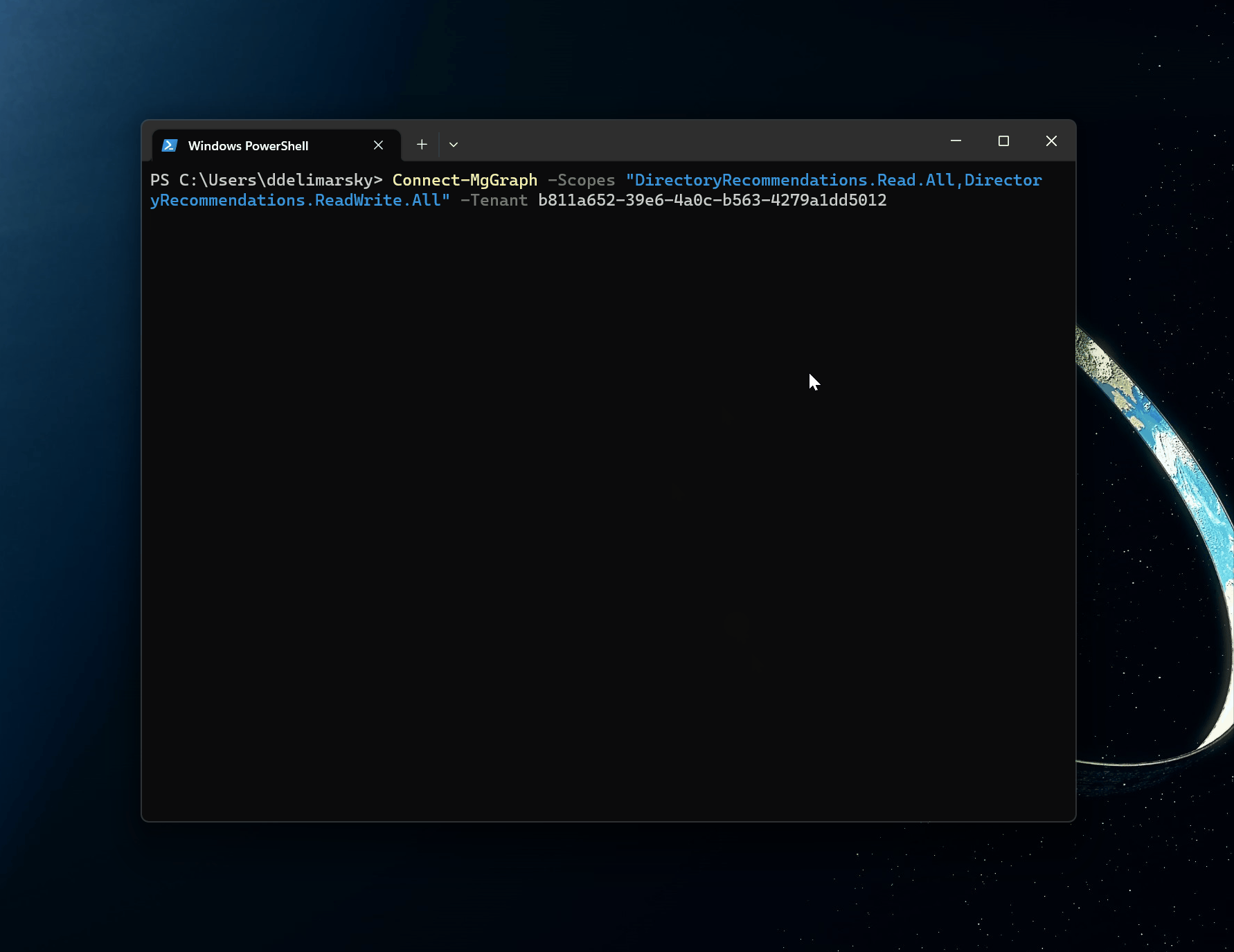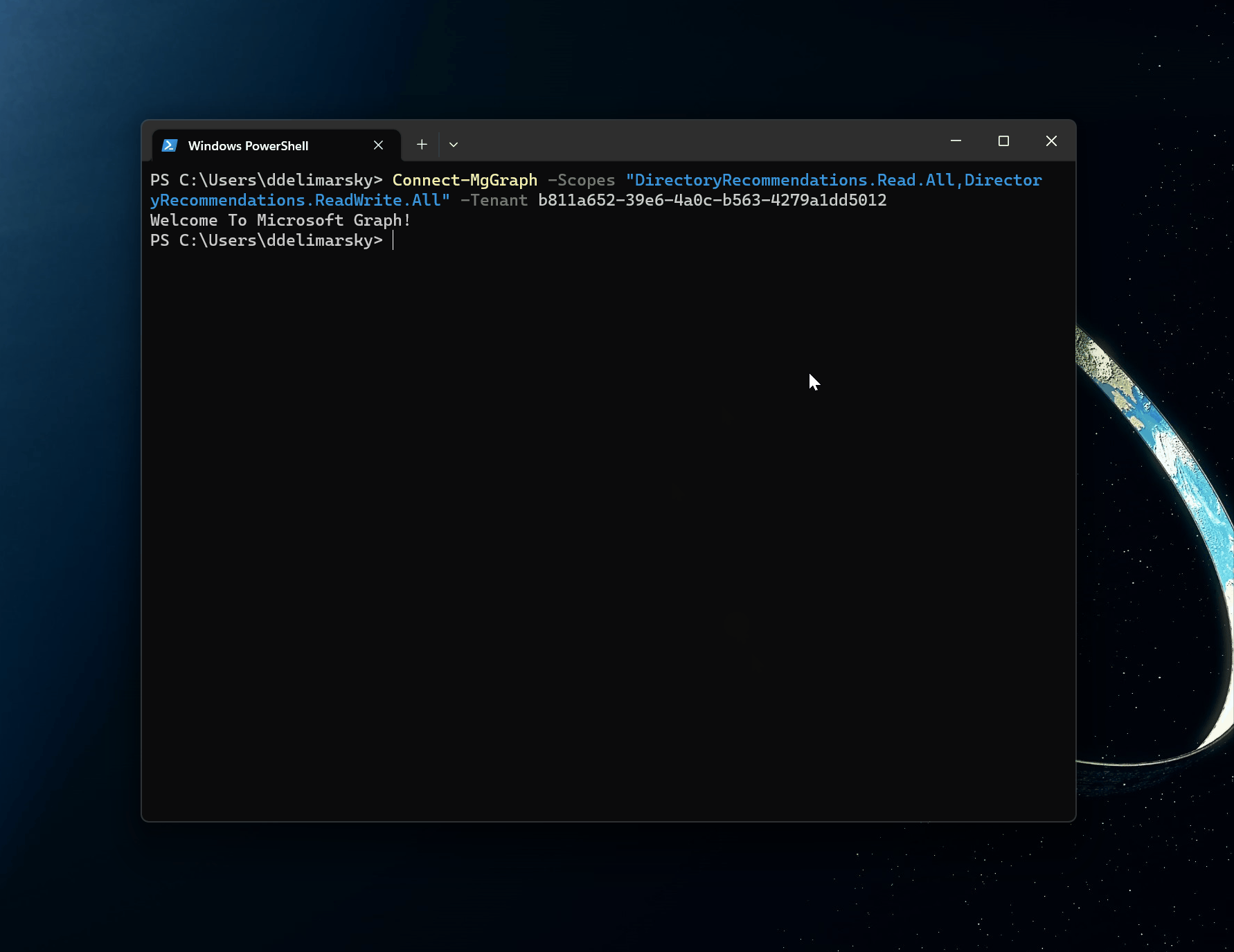
In the GIF above I would usually get a prompt asking which account to log in with but because I was previously authenticated I get an instant welcome message.
Next, because the API is in beta, I need to switch to the beta profile. No problem, all I need to do is run:
Select-MgProfile beta
This would, in turn, allow me to execute beta commands, such as Get-MgDirectoryRecommendation that would give me all of the insights from the REST API in a PowerShell-ready format (that can be filtered and sorted, when needed). Throw in a Format-List for good measure to see all of the metadata associated with the recommendation.
Get-MgDirectoryRecommendation -All | Format-List
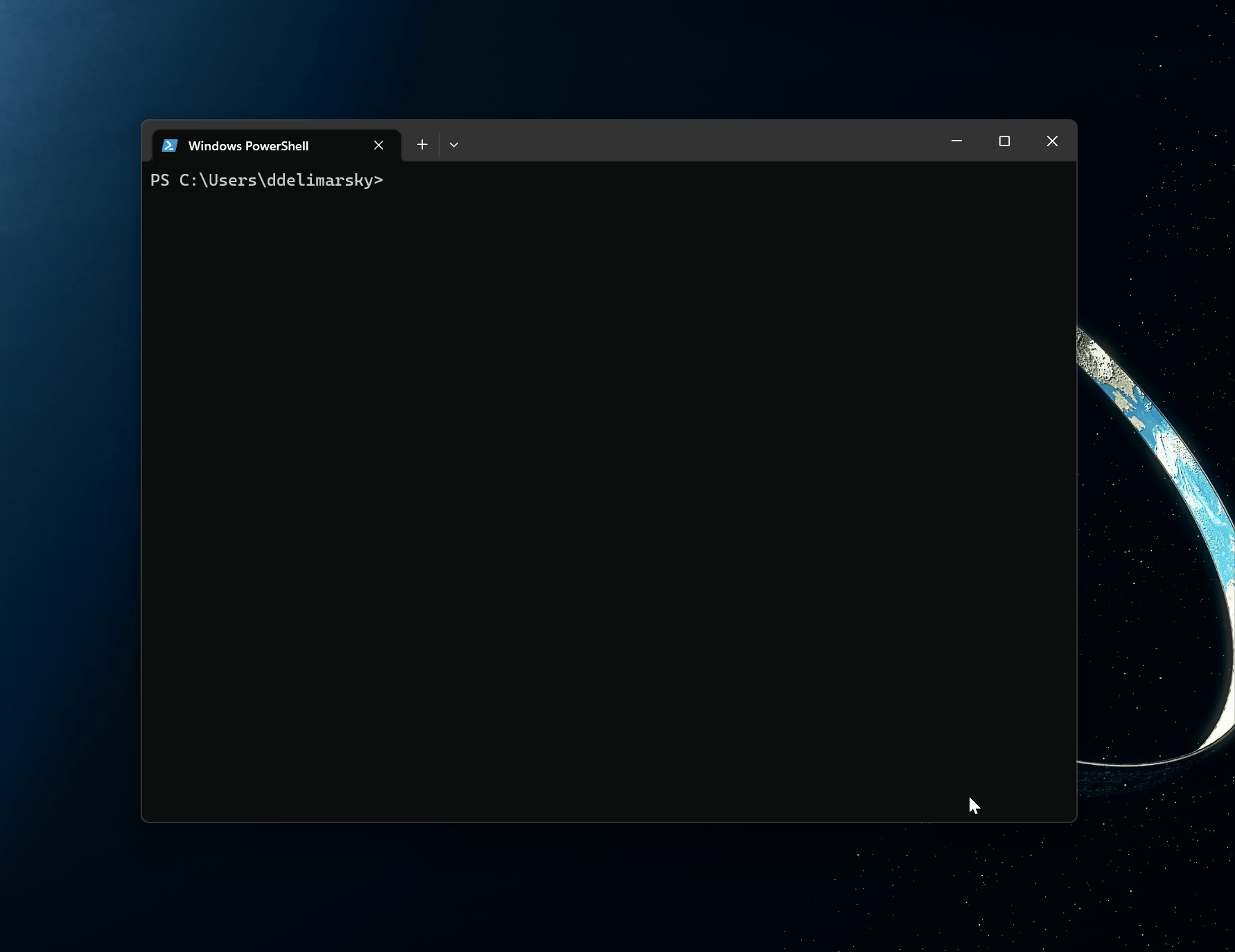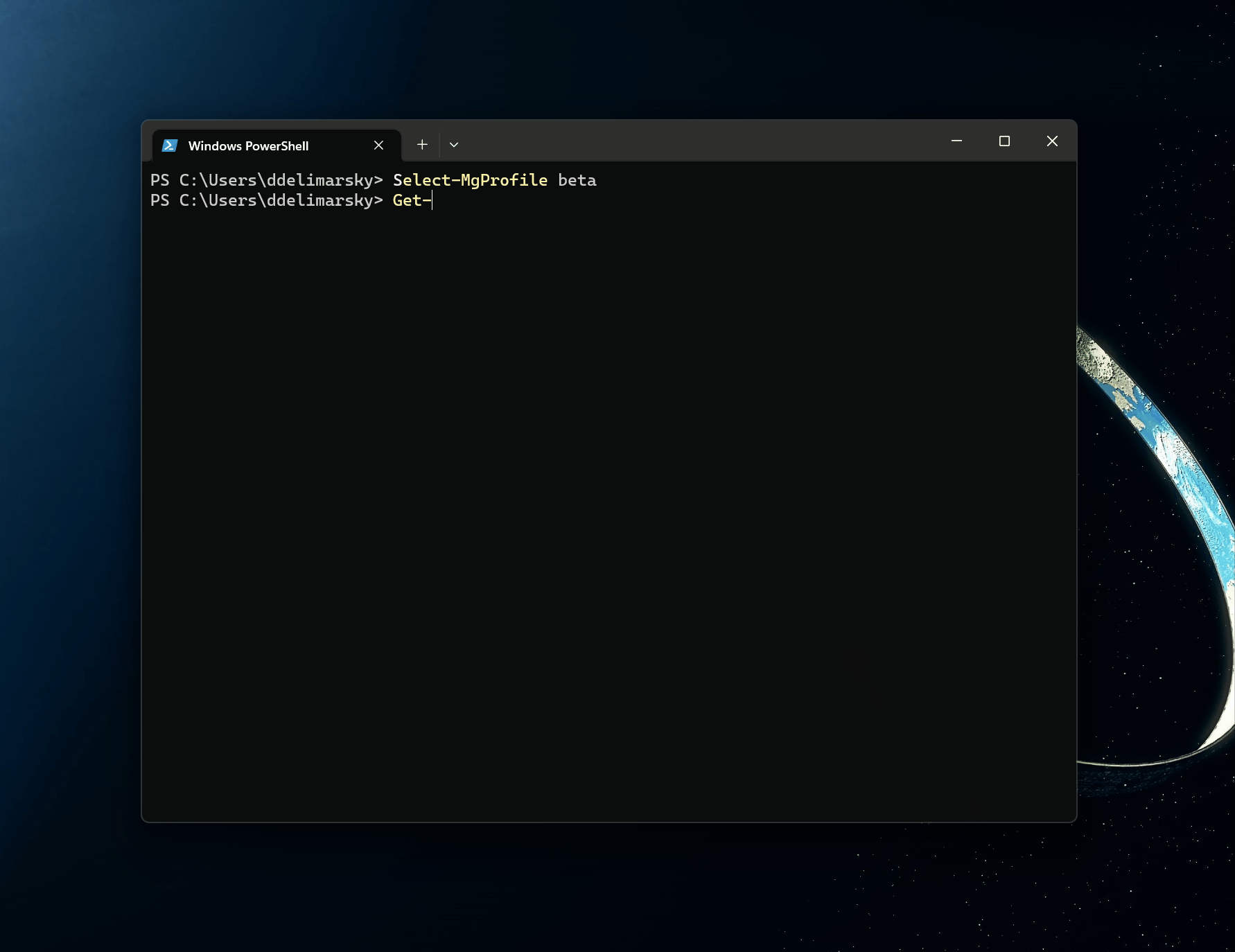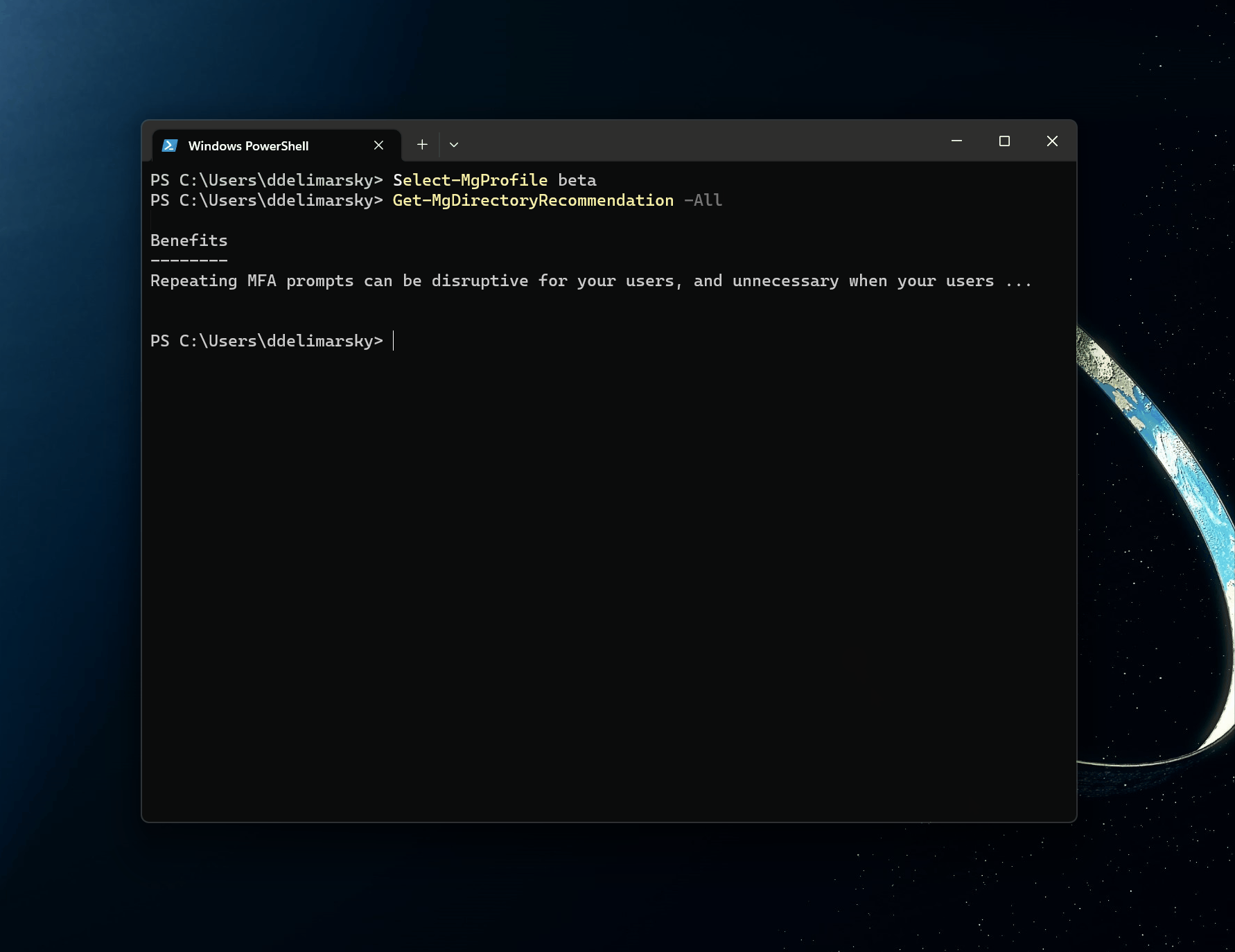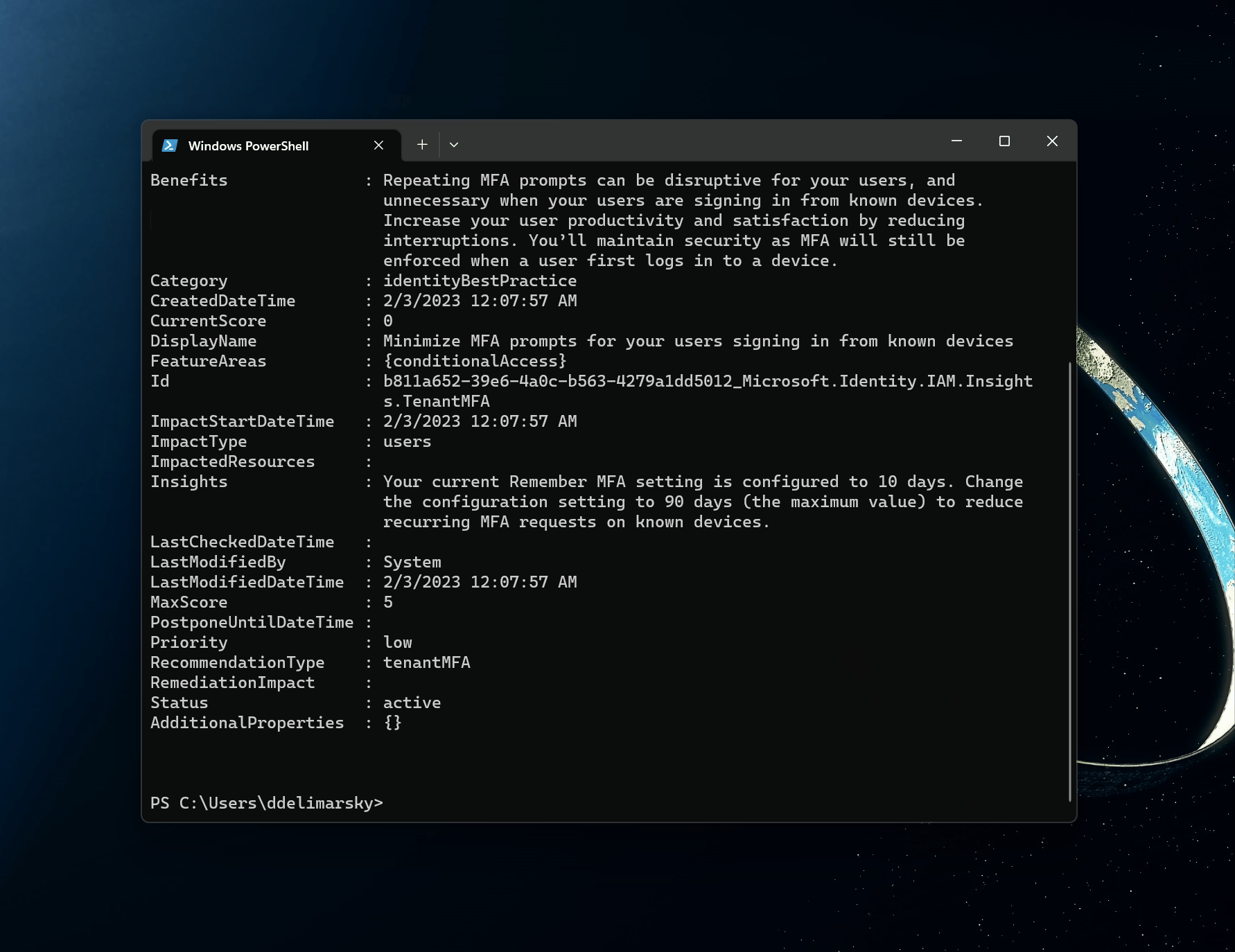
And there you have it - Azure AD Recommendations in your terminal. As more recommendations flow in, you can use standard PowerShell commands to extract useful information and generate reports, prioritize actions, and build custom internal alerts.